Section 3 of 3
Configure credentials¶
In this section, we'll create a Uffizzi Cloud account and connect it with your CI provider.
Uffizzi CI¶
If you're using Uffizzi CI, you will need to link to the Docker Compose template in your GitHub repository from the Uffizzi Dashboard. If you haven't already done so, sign up at Uffizzi Cloud, and then follow the steps to set up your account.
1. Connect the Uffizzi GitHub App
In this step you will install the Uffizzi GitHub App and grant Uffizzi access to the repositories you want to deploy. Login to Uffizzi, then navigate to Account > Settings > General, then select Configure next to the GitHub option.
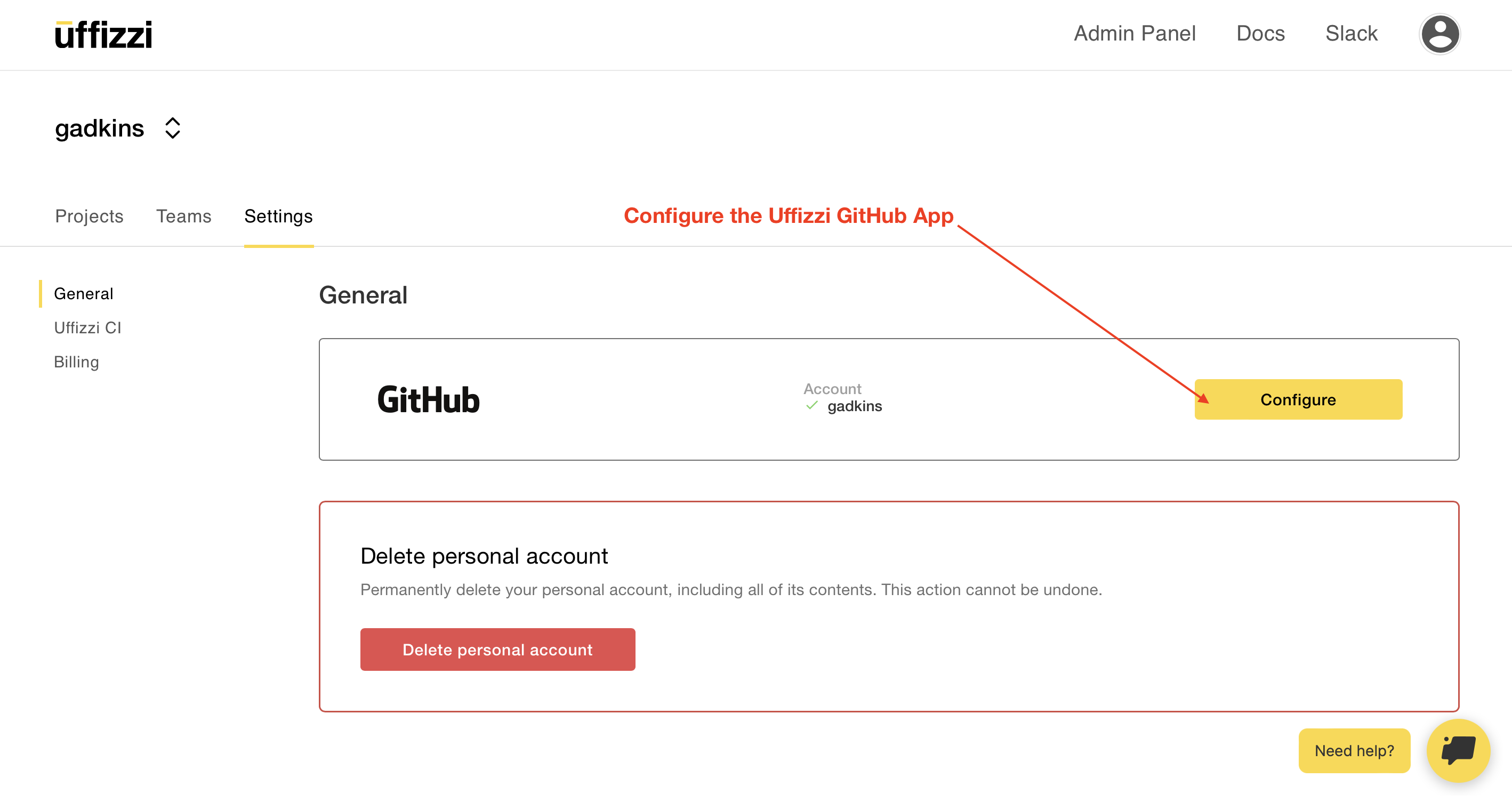
You'll be asked to Install Uffizzi Cloud, then grant access to your repositories.

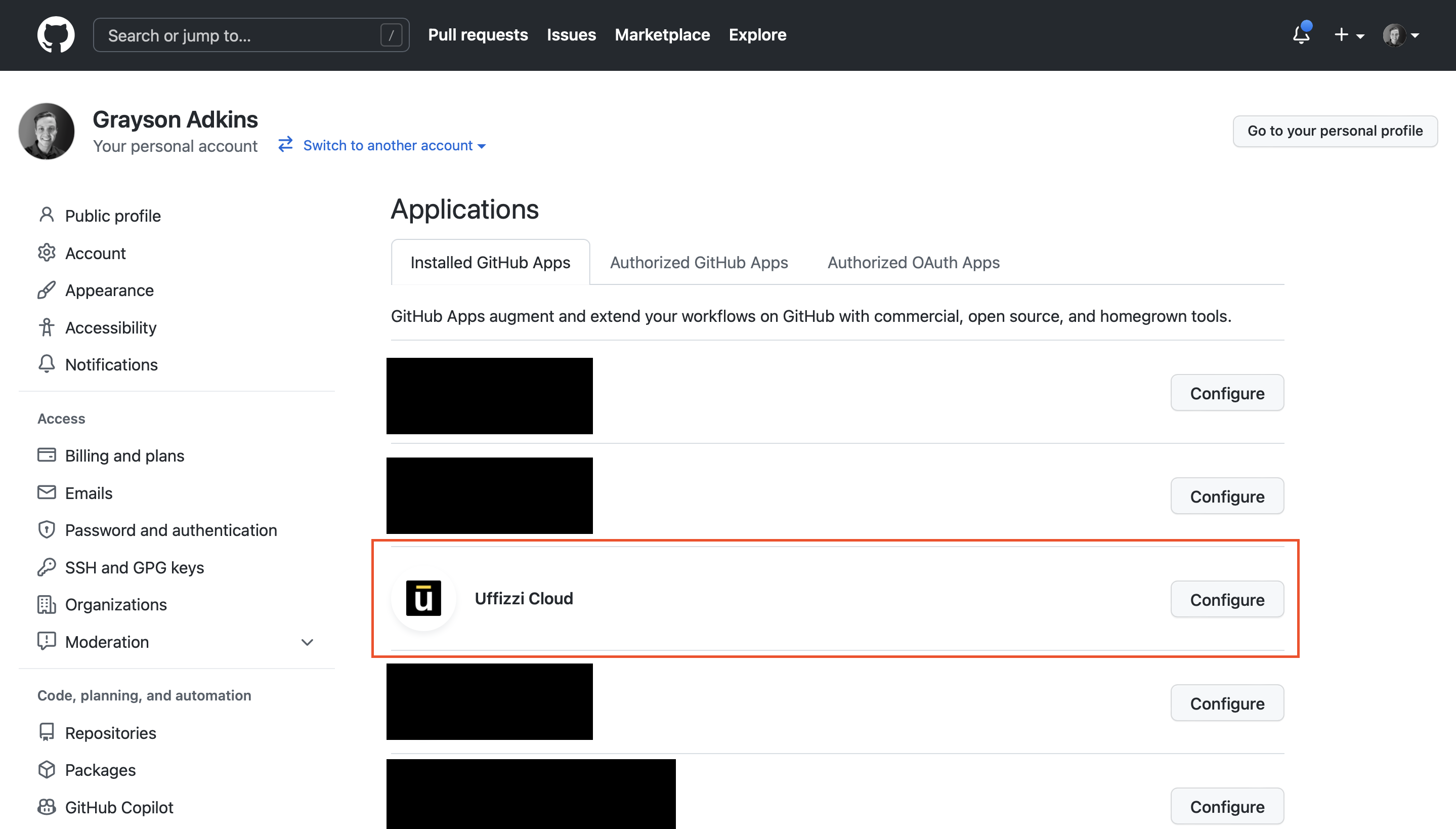
Similarly, you can manage the Uffizzi app installation from GitHub by navigating to Settings > Applications > Uffizzi Cloud > Configure
If the Docker Compose template you created in Section 1 references images stored in a private container registry, add those credentials in this step, as indicated in the screenshot below:
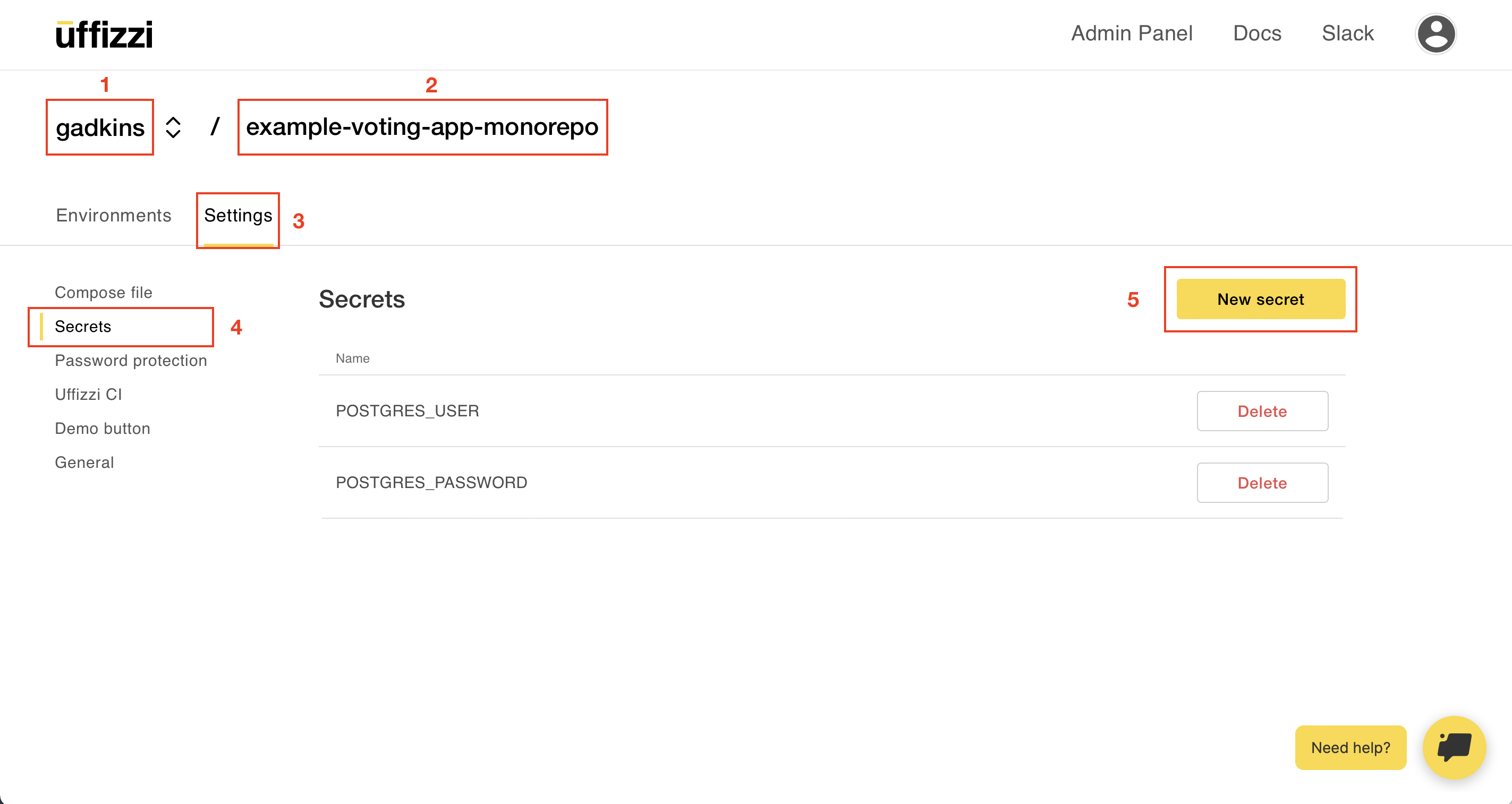
2. Add application secrets
If your compose file includes [application secrets](https://docs.uffizzi.com/references/compose-spec/#secrets), such as database credentials, you can add them in the Uffizzi Dashboard. Navigate to your project, then select Specs > Secrets > NEW SECRET. This will open a modal, where you can input your secrets as NAME=VALUE pairs. Be sure to add one secret per line, separatedy by = with no white spaces.
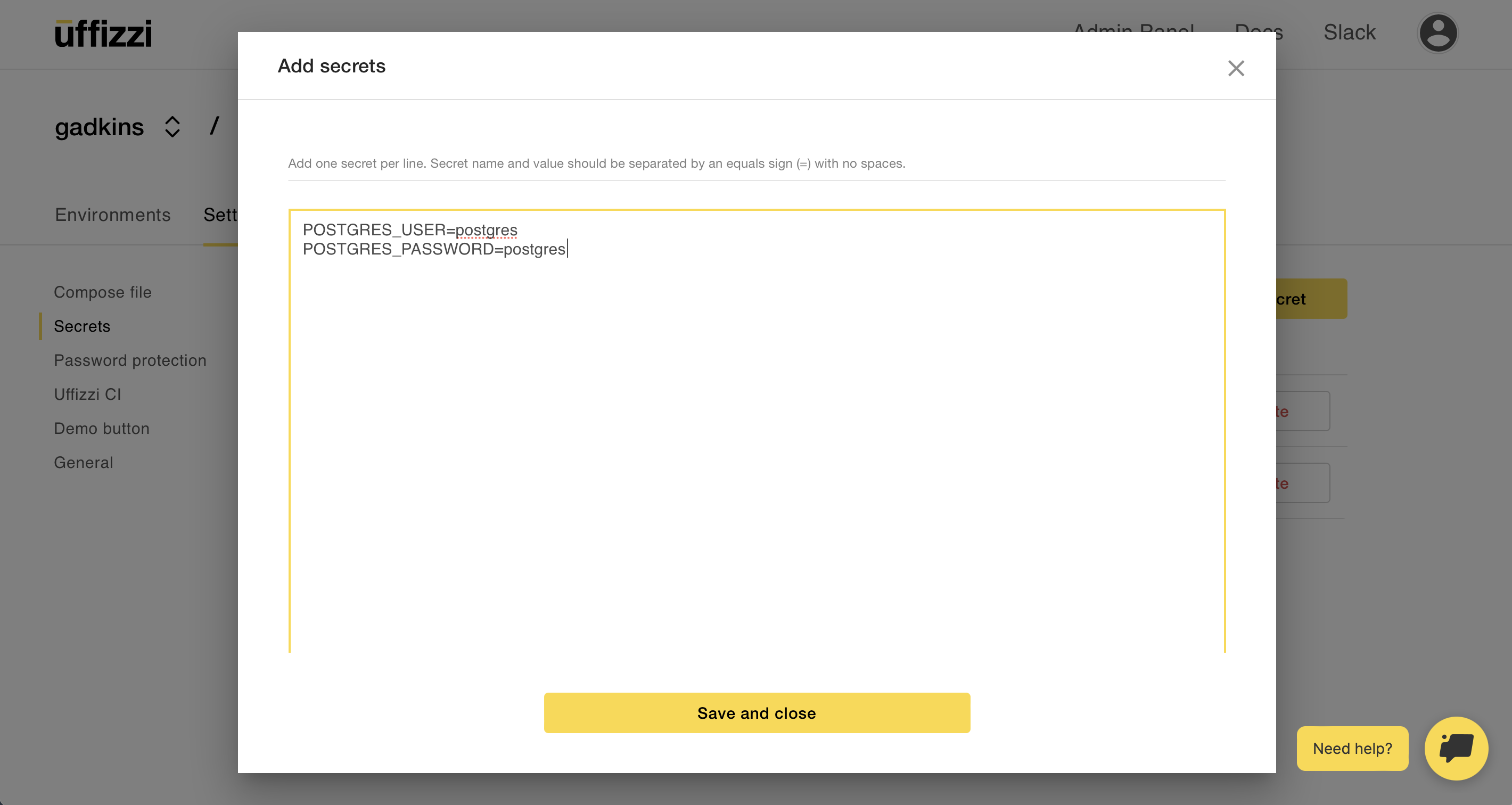
Once the secrets are saved, you will not be able to view or edit their values. To make changes to a secret, first delete the old secret, then create a new one.
3. Link to your Docker Compose template
In this final step, we'll link to our Docker Compose template that's stored in our GitHub repository. To do this, navigate to your project, then select Specs > Compose > NEW COMPOSE. Next, select the repository, branch (typically this is the branch you open pull requests against), and name of the compose file. Finally, select VALIDATE & SAVE.
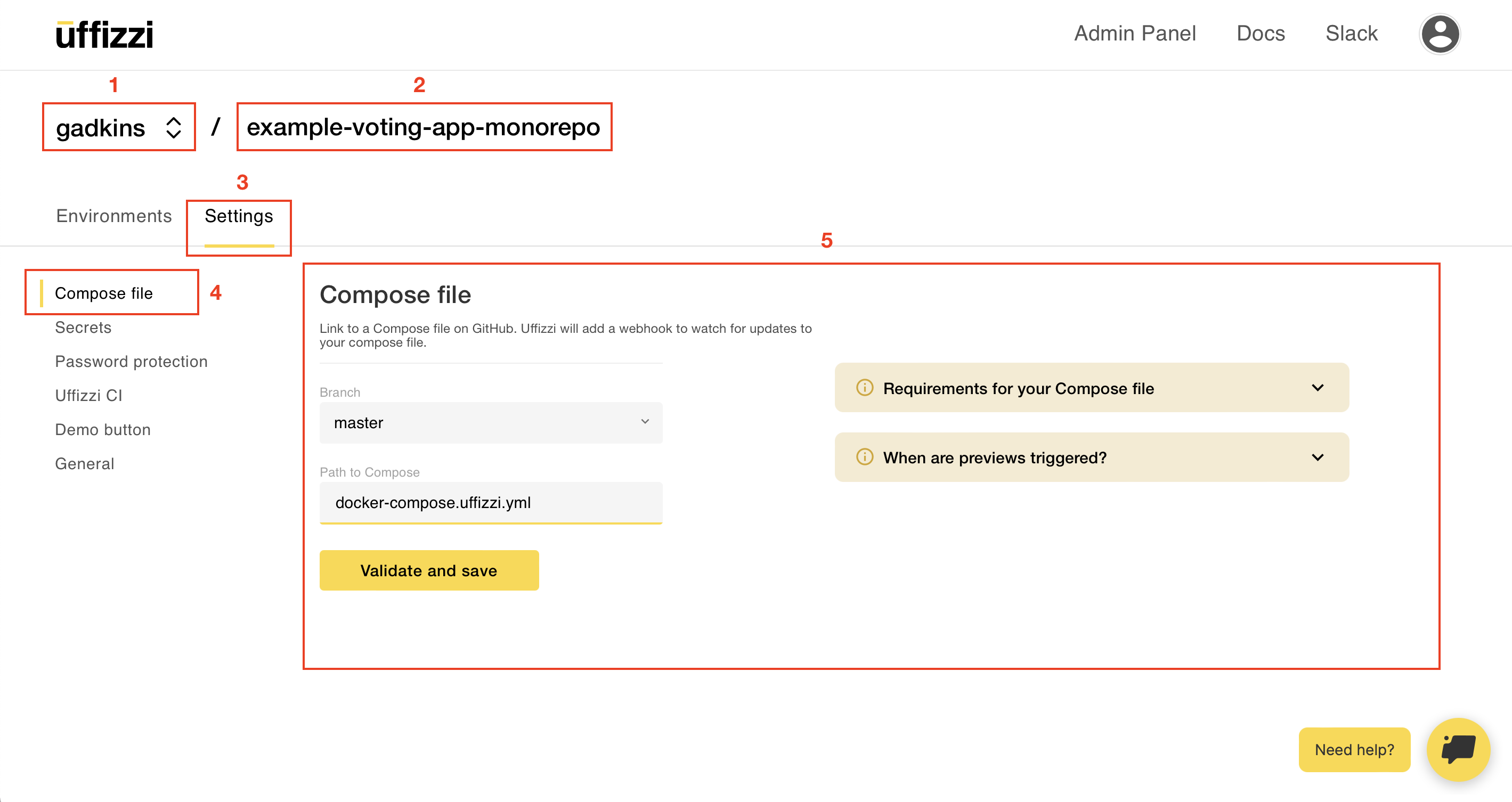
Note, if you did not add your secrets as described in the previous step, you will see a validation error with a link to add your secretes.
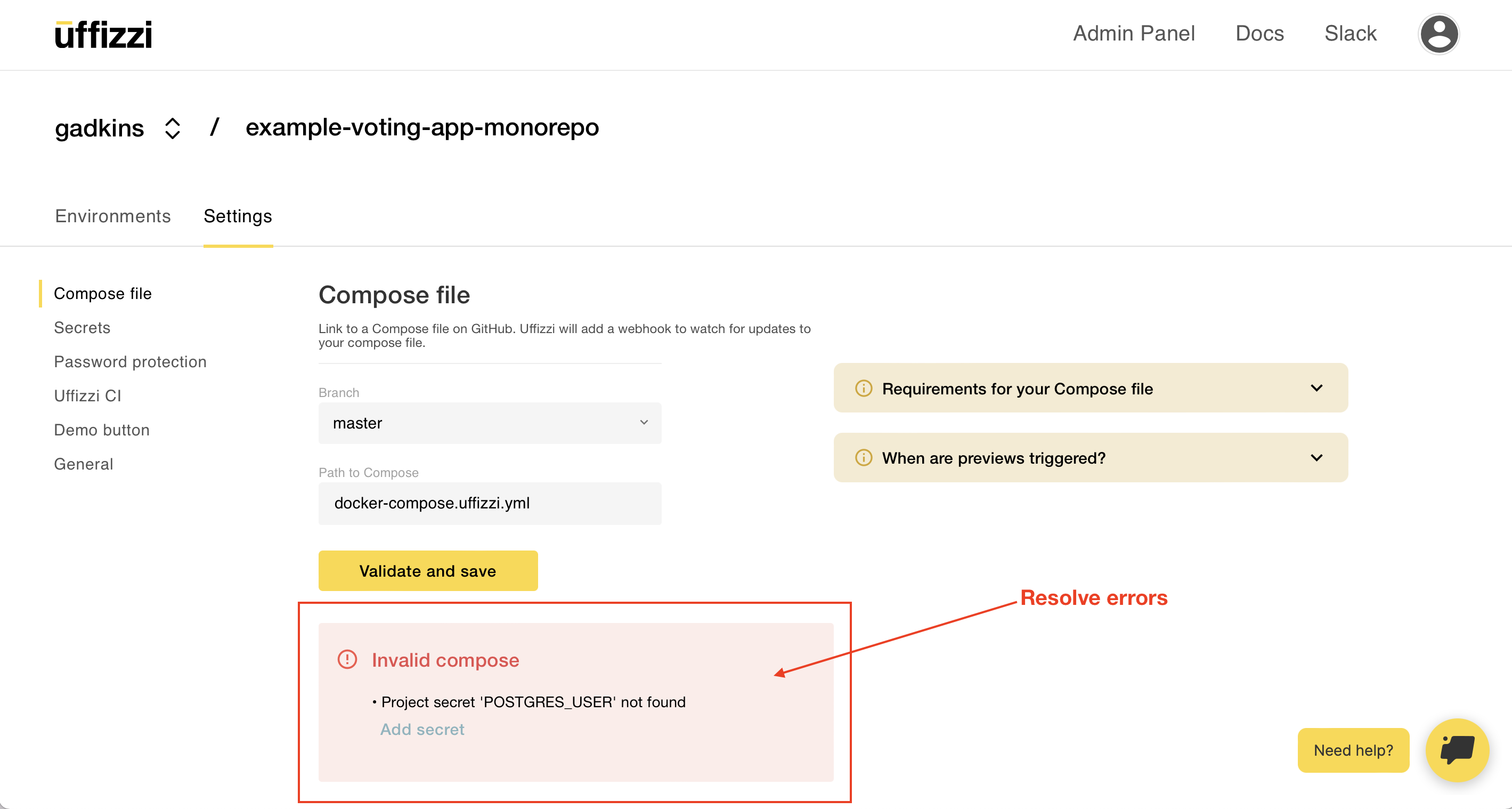
Once your compose file has been successfully added, you will see it in the Uffizzi Dashboard with a link to its source on GitHub. Any changes you make to this compose file on GitHub will be synced in the Uffizzi Dashboard.
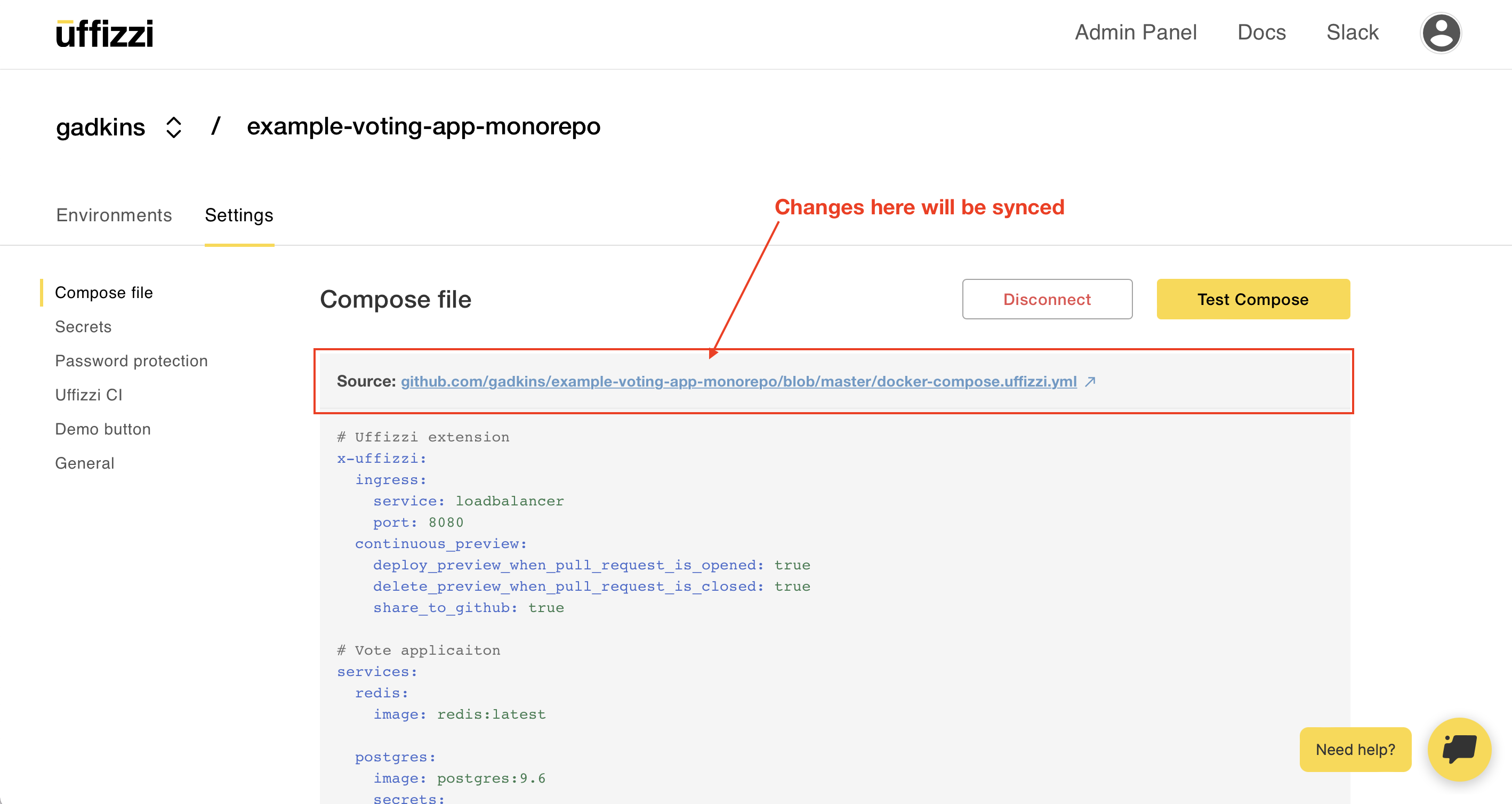
That's it! Uffizzi is now configured with your Docker Compose template. To test your setup, you can manually deploy your primary branch to an on-demand test environment using the Test Compose button in the Uffizzi Dashboard, or try opening a pull request on GitHub to deploy a feature branch.
Connect container registy credentials to Uffizzi¶
Follow this section if you're using an external container registry, such as GHCR, ECR, or Docker Hub, to store your built images (i.e. You are not relying on Uffizz CI to storage images for you).
How you add container registry credentials to Uffizzi depends on your registry of choice.
GitHub Container Registry (ghcr.io)¶
If you use GitHub Container Registry (ghcr.io), you will need to generate a GitHub personal access token with access to the read:packages scope. Once this token is generated, add it as a GitHub repository secret, then pass this value to the reusable workflow using the personal-access-token parameter, as described in the previous section.
Once you've created a personal access token, you should add it in your Uffizzi Account Settings.
Add GHCR personal access token in Account Settings
Login to Uffizzi, then navigate to Account > Settings > Registries, then select Configure next to the GHCR option.
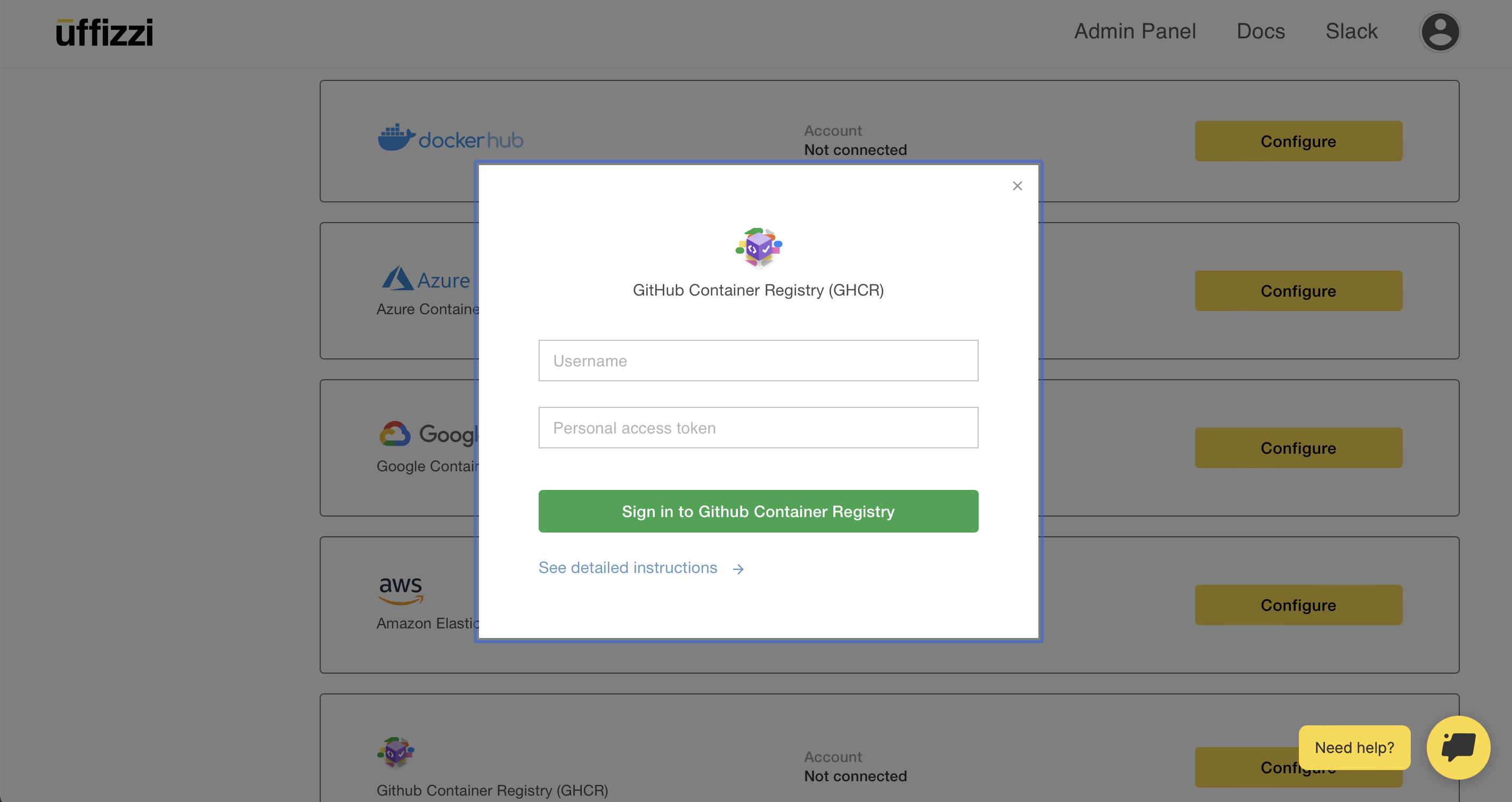
Enter your GitHub username and personal access token, then select Sign in to GitHub Container Registry.
ECR, ACR, GCR, Docker Hub¶
If you use Amazon ECR, Azure Container Registry (ACR), Google Container Registry (GCR), or Docker Hub, you should add your credentials as GitHub repository secrets.
See this AWS ECR example
If you use Amazon ECR, Azure Container Registry (ACR), Google Container Registry (GCR), or Docker Hub, you should add your credentials as GitHub repository secrets. In the highlighted example below, AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY are used:
[...]
jobs:
# Build and push app image
build-app:
name: Build and Push `app`
runs-on: ubuntu-latest
outputs:
tags: ${{ steps.meta.outputs.tags }}
steps:
- name: Login to ECR
uses: docker/login-action@v2
with:
registry: 263049488290.dkr.ecr.us-east-1.amazonaws.com
username: ${{ secrets.AWS_ACCESS_KEY_ID }}
password: ${{ secrets.AWS_SECRET_ACCESS_KEY }}
- name: Checkout git repo
uses: actions/checkout@v3
- name: Docker metadata
id: meta
uses: docker/metadata-action@v3
with:
images: 263049488290.dkr.ecr.us-east-1.amazonaws.com/app
- name: Build and Push Image to ECR
uses: docker/build-push-action@v2
with:
push: true
tags: ${{ steps.meta.outputs.tags }}
labels: ${{ steps.meta.outputs.labels }}
context: ./app
[...]
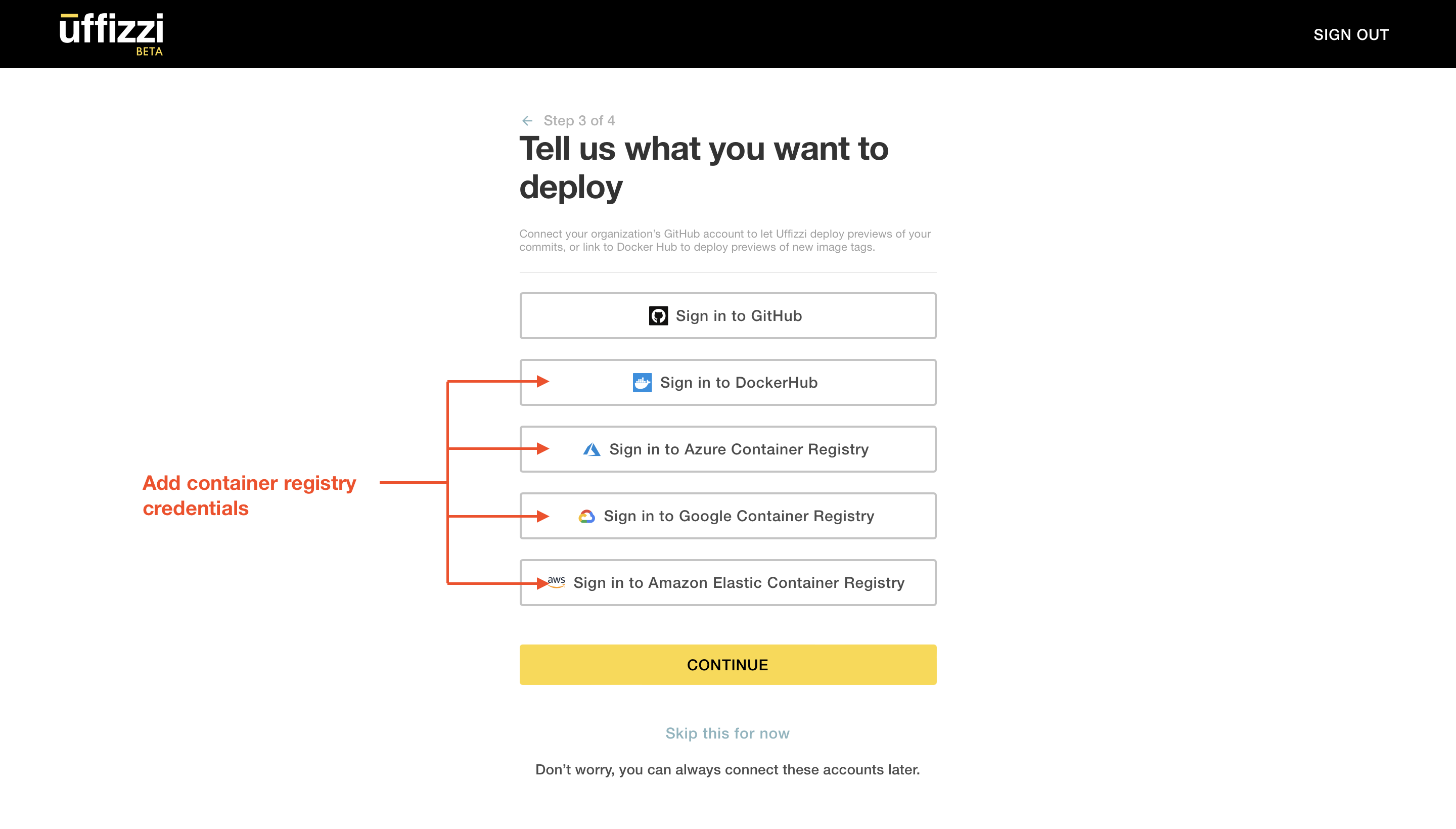
Now, we need to add these same credentials in the Uffizzi Dashboard. In Step 3 of 4 of the account setup guide, you are asked to connect to various external services, as shown below. Select the Sign in option for your registry provider(s) of choice, then enter your credentials. For example, to add AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY, select Sign in to Amazon Elastic Container Registry.
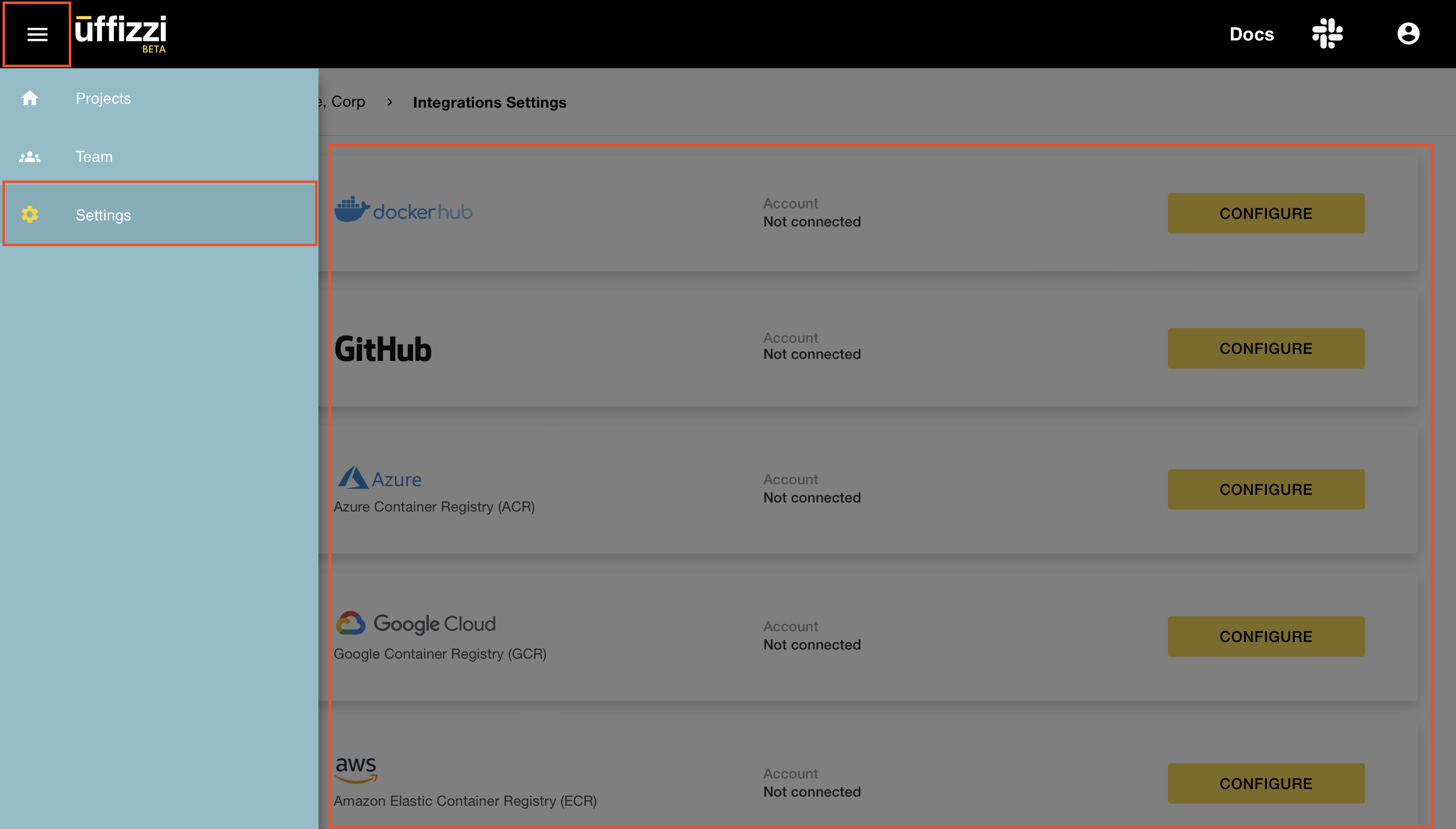
After account setup, you can make changes to your credentials by selecting Menu (three horizontal lines) > Settings > Integrations > CONFIGURE/DISCONNECT.
That's it! Your pipeline is now configured to use Uffizzi. To test your pipeline, try opening a new pull request.